Still remember 90s MTV Europe VJs? (Part 2)
While updating the video to my first MTV Europe VJs post I stumbled over Marijne van der Vlugt‘s band Salad.
Install a Python development environment on Windows
2023-10-27: Updated to use pipx and now manual PATH fiddling. I was trying to set up a Windows-native Python development environment with Poetry. Since Microsoft is doing a lot of Python extensions for VSCode I expected this to be a breeze. Well… there are some stumbling blocks along the way. Anyway, here’s how I got…
Programmer’s Utilities Guide recreation

After recreating the CP/M User’s Guide, then the CP/M Programmer’s Guide, and the CP/M System Guide I thought I would be done. But then the System Guide referenced yet another Guide: the Programmer’s Utilities Guide. For now this will be the last of my Digital Research manual recreations. This guide is based on this scan…
CP/M System Guide recreation

This is the third part of my CP/M manual recreation project. After recreating the CP/M User’s Guide, and then the CP/M Programmer’s Guide, this is now the System Guide. Like with the previous two recreations, I based this on the OCRed version of the CP/M System Guide. Files CP/M System Guide (interactive PDF with hyperlinks…
CP/M Programmer’s Guide recreation

This is the second part of my CP/M manual recreation project. After recreating the CP/M User’s Guide first, this is now the Programmer’s Guide. As with the first part, I based my recreation on the OCRed versions on the OCRed version of the CP/M Programmers’s Guide. Files CP/M Programmers’s Guide (interactive PDF with hyperlinks for…
JiffyDOS User’s Manual

Sometime in 2016 I recreated the JiffyDOS User’s Manual in InDesign. This was just an excercise to get more comfortable with InDesign. Long story short, here is the result: JiffyDOS 6 Users Manual (interactive PDF version for online reading) JiffyDOS 6 Users Manual (print-ready version with crop marks) Use them for good, not for evil.
CP/M User’s Manual recreation

My original CP/M manuals are starting to fall apart. There are scanned and OCRed versions of these manuals available on the internet but these look plain and contain errors that were introduced by OCR. Based on the OCRed version of the CP/M User’s Manual I tried to faithfully recreate the old manual. The resulting PDFs…
SSH on Windows

You’ve mastered all the SSH settings on your Linux/Mac and suddenly you’re thrust into the Windows world and need to access another machine via SSH. Old-school Windows users will probably download PuTTY. That should allow the most basic SSH operations. But once you need to do some more advanced stuff, you’ll also need to download…
Use Windows Terminal by default

Have you ever thought that the default Windows console host is a clunky old piece of garbage? Choosing the font or colors is awkward at best. And it can’t be even resized horizontally. What a piece of crap! Microsoft seems to have finally realized that and started the Windows Terminal project. Once you install Windows…
Pfsense Gateway Latency with Telegraf

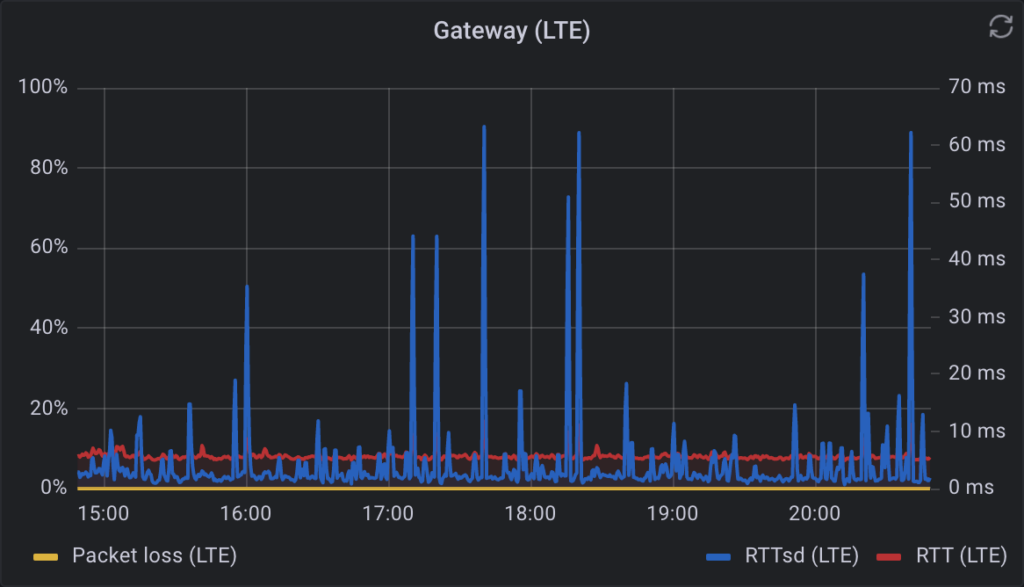
Some years ago I started using the Telegraf package on pfSense and was disappointed to find out that it didn’t report the gateway latencies. So I wrote a quick&dirty Python 2 script that would parse the output of pfSense’s dpinger and output it in a format that Telegraf could send to InfluxDB. With the most…
Privacy Overview
This website uses cookies to improve your experience while you navigate through the website. Out of these, the cookies that are categorized as necessary are stored on your browser as they are essential for the working of basic functionalities of the website. We also use third-party cookies that help us analyze and understand how you use this website. These cookies will be stored in your browser only with your consent. You also have the option to opt-out of these cookies. But opting out of some of these cookies may affect your browsing experience.
Necessary cookies are absolutely essential for the website to function properly. These cookies ensure basic functionalities and security features of the website, anonymously.
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-advertisement | 1 year | Set by the GDPR Cookie Consent plugin, this cookie is used to record the user consent for the cookies in the "Advertisement" category . |
| cookielawinfo-checkbox-analytics | 1 year | Set by the GDPR Cookie Consent plugin, this cookie is used to record the user consent for the cookies in the "Analytics" category . |
| cookielawinfo-checkbox-functional | 1 year | The cookie is set by the GDPR Cookie Consent plugin to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 1 year | Set by the GDPR Cookie Consent plugin, this cookie is used to record the user consent for the cookies in the "Necessary" category . |
| cookielawinfo-checkbox-others | 1 year | Set by the GDPR Cookie Consent plugin, this cookie is used to store the user consent for cookies in the category "Others". |
| cookielawinfo-checkbox-performance | 1 year | Set by the GDPR Cookie Consent plugin, this cookie is used to store the user consent for cookies in the category "Performance". |
| CookieLawInfoConsent | 1 year | Records the default button state of the corresponding category & the status of CCPA. It works only in coordination with the primary cookie. |
Functional cookies help to perform certain functionalities like sharing the content of the website on social media platforms, collect feedbacks, and other third-party features.
Performance cookies are used to understand and analyze the key performance indexes of the website which helps in delivering a better user experience for the visitors.
Analytical cookies are used to understand how visitors interact with the website. These cookies help provide information on metrics the number of visitors, bounce rate, traffic source, etc.
Advertisement cookies are used to provide visitors with relevant ads and marketing campaigns. These cookies track visitors across websites and collect information to provide customized ads.
Other uncategorized cookies are those that are being analyzed and have not been classified into a category as yet.
| Cookie | Duration | Description |
|---|---|---|
| _pk_id.1.cfaf | 1 year 27 days | No description |
| _pk_ses.1.cfaf | 30 minutes | No description |